About Me
-
I’m Prakhar, internet often know me as prakhar0x01 (Ghost).
-
Reported and responsibly disclosed 100+ valid security vulnerabilities across large-scale production systems, resulting in security fixes across Fortune 500 and government organizations including Google, United Nations, Sony, Starbucks, US Department Of Defence and more..(confidential).
-
Identified and responsibly disclosed high-impact vulnerabilities including RCE, IDOR, auth bypass, privilege escalation, SSRF, and PII exposure(1M+ users) in real-world environments.
-
CVE author with 5 assigned CVEs affecting widely used software (2025). Top 5% on TryHackMe Platform.Ranked among Top 100 security researchers in India (2025) on HackerOne leaderboards
-
Addtionally, I’m Interested in Gaming, Psychology & Philosophy, Aviation, DarkWeb and more. I occasionally play CTFs on TryHackMe & HackingHub. So ping me, If you’re interested in collaborating or just want to discuss about any of these topics, feel free to reach out!
Track Record …

PII Leak – 1 Million User Records

PII Leak & Account Takeovers
Multiple Account Takeovers

Internal Server Access (SSRF)

Business Logic Exploitation
Information Disclosure

Privilege Escalation

Information Disclosure
...and more (confidential)
Projects …
1. Deceptor - An automated script to discover and bypass Web-Cache Deception
An automated script to discover and bypass Web-Cache Deception
2. Approach - An automated script to perform daily recon tasks
Approach is a beginner-friendly script that condenses manual reconnaissance into a single command. By orchestrating popular tools, it automatically filters for live targets and identifies high-value assets like login portals. Designed for speed and precision, so you can focus on finding vulnerabilities rather than running scripts.
3. TorNet Granted - Enumerating Onion URLs
Python-based web application project for exploring and analyzing the dark web within the TOR (The Onion Router) network. With a focus on threat intelligence and cybersecurity, our software provides a user-friendly interface for discovering, validating & analyzing onion URLs, DOM rendering, Enumerating Onion URLs and scheduling automated tasks init.
4. Xpose - Deanonymization Simulation on DarkWeb Operators
Xpose is a powerful software simulation for performing advanced deanonymization techniques, designed to trace the operators behind illegal dark web sites. The system includes both a web app and CLI (Command Line Interface) to offer flexibility and reliability.
Licenses & Certifications
| Certification | Issued | Issuing Organisation | ||
|---|---|---|---|---|
| Penetration Testing | Sep 2022 | Charles Struts University | ||
| Certified In CyberSecurity | Oct 2022 | ISC2 | ||
| Certified AppSec Practitioner | Jan 2023 | The SecOps Group | ||
| National Finalist - Smart India Hackathon (SIH) | Dec 2023 | Government Of India | ||
| National Finalist - Pentathon 2024 | Mar 2024 | Government Of India | ||
| National Finalist - Pentathon 2025 | Apr 2025 | Government Of India | ||
| CVE-2025-64489 | Nov 2025 | SuiteCRM | ||
| CVE-2025-64490 | Nov 2025 | SuiteCRM |
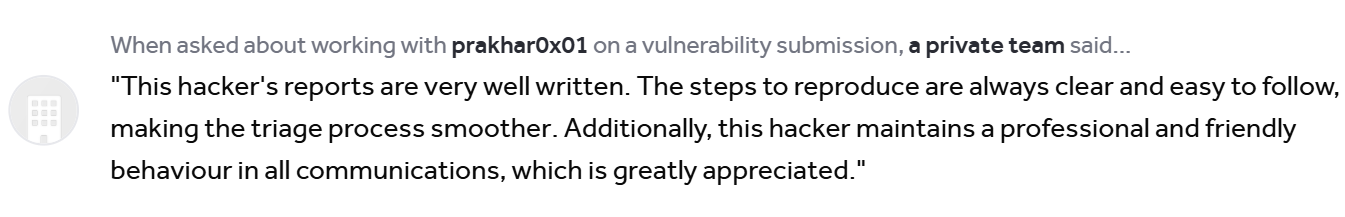
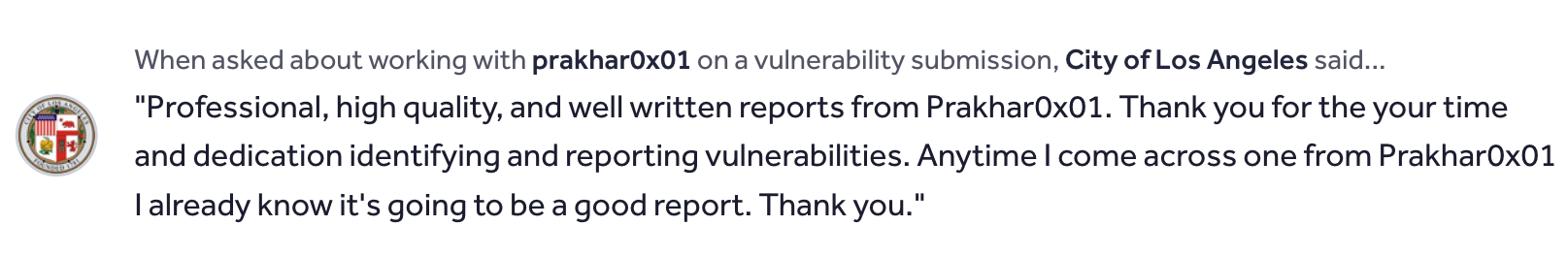
Testimonials…
Explore …
Interested in exploring some of my work? Here are a few resources:
- HackerOne Profile: Actual Work.
- GitHub Profile: Explore my Projects, contributions, and repositories.
- My Write-Ups: Read write-ups on some of my interesting Security Research.
- My Blogs: Read some of my blog posts related to psychology & philosophy.
- Contact Me: Feel free to reach out for collaborations or inquiries.
